A Sneaky Ad Scam Tore Through 11 Million Phones
Every time you open an app or website, a flurry of invisible processes takes place without you knowing. Behind the scenes, dozens of advertising companies are jostling for your attention: They want their ads in front of your eyeballs. For each ad, a series of instant auctions often determines which ads you see. This automated advertising, often known as programmatic advertising, is big business, with $418 billion spent on it last year. But it’s also ripe for abuse.
Security researchers today revealed a new widespread attack on the online advertising ecosystem that has impacted millions of people, defrauded hundreds of companies, and potentially netted its creators some serious profits. The attack, dubbed Vastflux, was discovered by researchers at Human Security, a firm focusing on fraud and bot activity. The attack impacted 11 million phones, with the attackers spoofing 1,700 app and targeting 120 publishers. At its peak, the attackers were making 12 billion requests for ads per day.
“When I first got the results for the volume of the attack, I had to run the numbers multiple times,” says Marion Habiby, a data scientist at Human Security and the lead researcher on the case. Habiby describes the attack as both one of the most sophisticated the company has seen and the largest. “It is clear the bad actors were well organized and went to great lengths to avoid detection, making sure the attack would run as long as possible—making as much money as possible,” Habiby says.
Online and mobile advertising is a complex, often murky business. But it generates piles of money for those involved. Every day billions of ads are placed on websites and in apps—advertisers or ad networks pay to have their ads displayed and make money when people click on them or see them—and much of this is done as you open a website or an app.
Vastflux was first detected by Human Security researcher Vikas Parthasarathy in the summer of 2022 while he was investigating a different threat. Habiby says operating the fraud involved multiple steps, and the attackers behind it took a range of measures to avoid being caught out.
First, the group behind the attack—which Human Security hasn’t named due to ongoing investigations—would target popular apps and try to buy an advertising slot within them. “They were not trying to hijack an entire phone, or an entire app, they were literally going through one ad slot,” Habiby says.
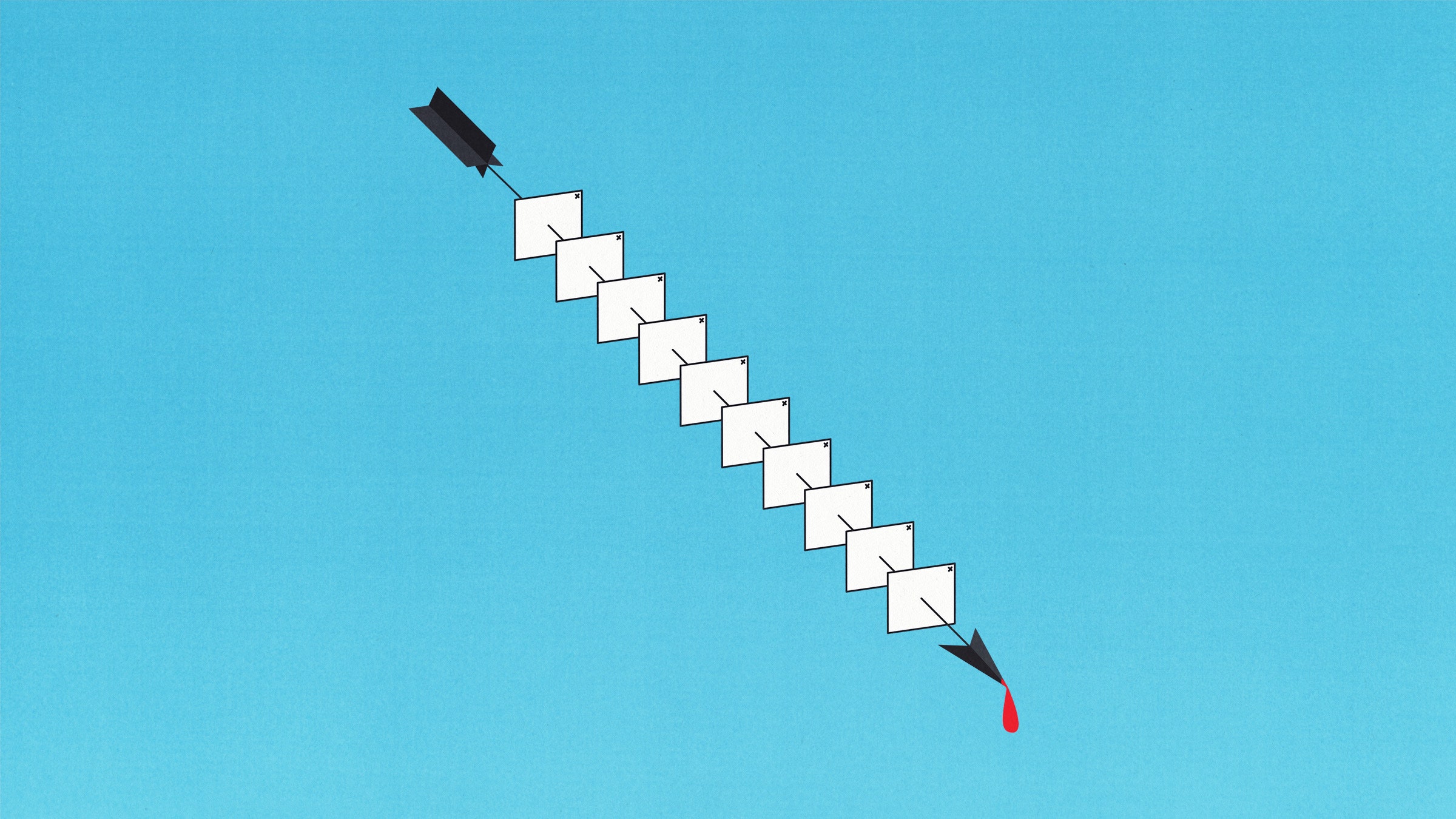
Once Vastflux won the auction for an ad, the group would insert some malicious JavaScript code into that ad to stealthily allow multiple video ads to be stacked on top of each other.
Put simply, the attackers were able to hijack the advertising system so that when a phone was displaying an ad within an affected app, there would actually be up to 25 ads placed on top of each other. The attackers would get paid for each ad, and you would only see one ad on your phone. However, your phone battery would drain faster than usual as it processed all the fraudulent ads.